Calendly Security Concerns
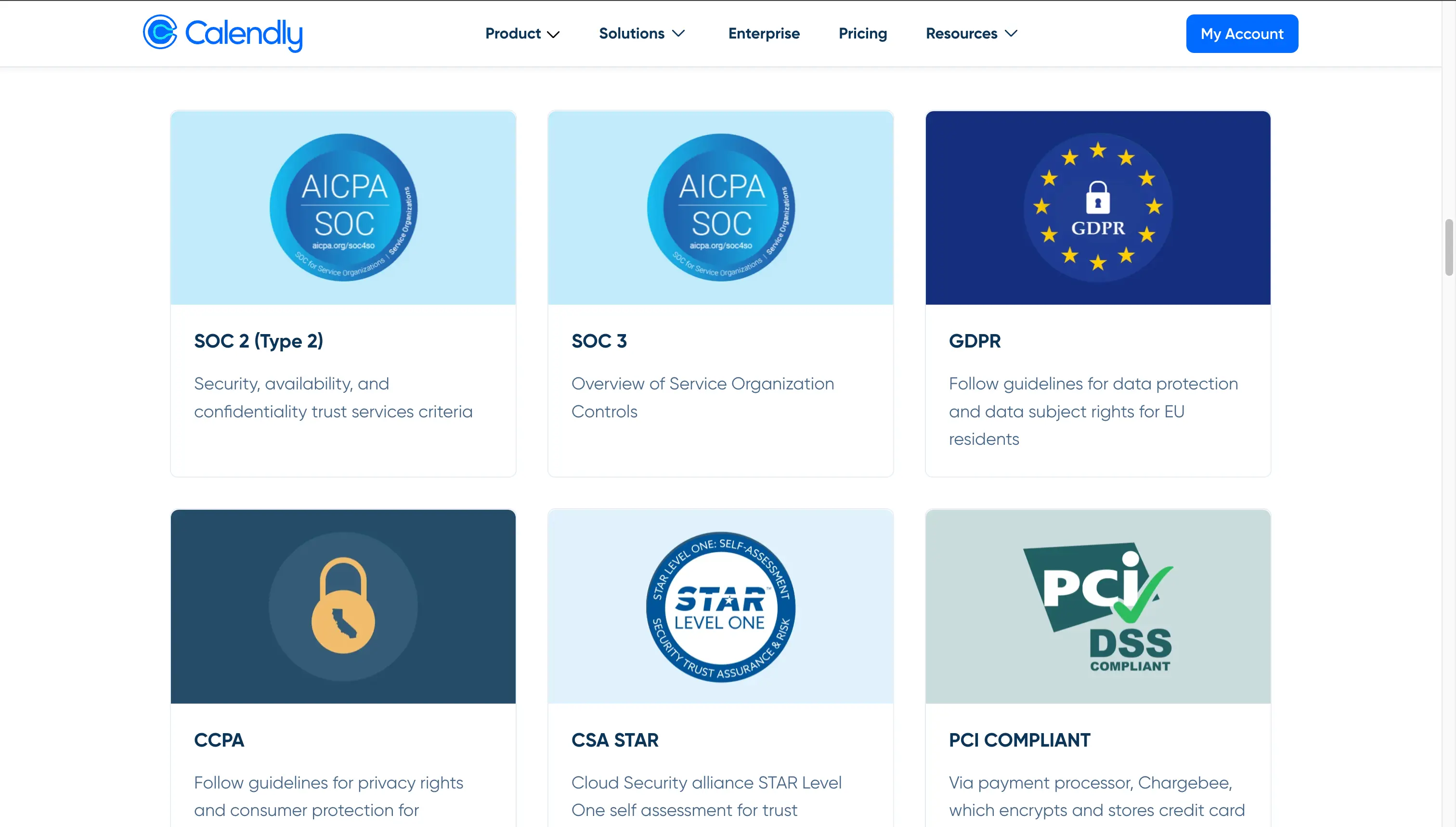
Calendly Security Concerns - Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Calendly’s dedicated team constantly enhances our security. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Learn about data breaches, cyber attacks, and security incidents involving. Security and the safeguarding of customer data shouldn’t be an afterthought. Compare calendly's security performance with other companies.
Learn about data breaches, cyber attacks, and security incidents involving. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Compare calendly's security performance with other companies. Security and the safeguarding of customer data shouldn’t be an afterthought. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Calendly’s dedicated team constantly enhances our security.
Security and the safeguarding of customer data shouldn’t be an afterthought. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Learn about data breaches, cyber attacks, and security incidents involving. Calendly’s dedicated team constantly enhances our security. Compare calendly's security performance with other companies.
urlscan.io
Security and the safeguarding of customer data shouldn’t be an afterthought. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Calendly’s dedicated team constantly enhances our security. Learn about data breaches, cyber attacks, and security incidents involving. Compare calendly's security performance with other companies.
How to use Calendly to schedule important calls and automate your
Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Learn about data breaches, cyber attacks, and security incidents involving. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Security and the safeguarding of customer data shouldn’t be an afterthought. Compare calendly's security performance with other companies.
Calendly Single Sign On (SSO) SAML OAuth LDAP MFA
Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Security and the safeguarding of customer data shouldn’t be an afterthought. Compare calendly's security performance with other companies. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Calendly’s dedicated team constantly enhances our security.
Calendly Scheduling software could save you about 50 hours a year
Security and the safeguarding of customer data shouldn’t be an afterthought. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Learn about data breaches, cyber attacks, and security incidents involving. Compare calendly's security performance with other companies.
Calendly Qr Code Printable Word Searches
Calendly’s dedicated team constantly enhances our security. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Security and the safeguarding of customer data shouldn’t be an afterthought. Learn about data breaches, cyber attacks, and security incidents involving. Compare calendly's security performance with other companies.
The Best Calendly Alternatives for Your Small Business
Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Calendly’s dedicated team constantly enhances our security. Security and the safeguarding of customer data shouldn’t be an afterthought. Compare calendly's security performance with other companies. We follow strict security practices, keeping minimal customer data and using only the necessary permissions.
Calendly Delivers a Seamless Employee Experience With DocuSign
Security and the safeguarding of customer data shouldn’t be an afterthought. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Calendly’s dedicated team constantly enhances our security. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Learn about data breaches, cyber attacks, and security incidents involving.
Calendly User and Company Stats (2023) MKs Guide
Compare calendly's security performance with other companies. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Security and the safeguarding of customer data shouldn’t be an afterthought. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Learn about data breaches, cyber attacks, and security incidents involving.
The 6 Best Calendly Alternatives (Reviewed) in 2024 Idea Strider
Learn about data breaches, cyber attacks, and security incidents involving. Calendly’s dedicated team constantly enhances our security. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Security and the safeguarding of customer data shouldn’t be an afterthought.
Calendly vs Which is the best scheduling platform?
Learn about data breaches, cyber attacks, and security incidents involving. Calendly’s dedicated team constantly enhances our security. We follow strict security practices, keeping minimal customer data and using only the necessary permissions. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials. Compare calendly's security performance with other companies.
We Follow Strict Security Practices, Keeping Minimal Customer Data And Using Only The Necessary Permissions.
Security and the safeguarding of customer data shouldn’t be an afterthought. Compare calendly's security performance with other companies. Learn about data breaches, cyber attacks, and security incidents involving. Phishing actors abuse calendly to send fake emails with malicious links and steal microsoft login credentials.