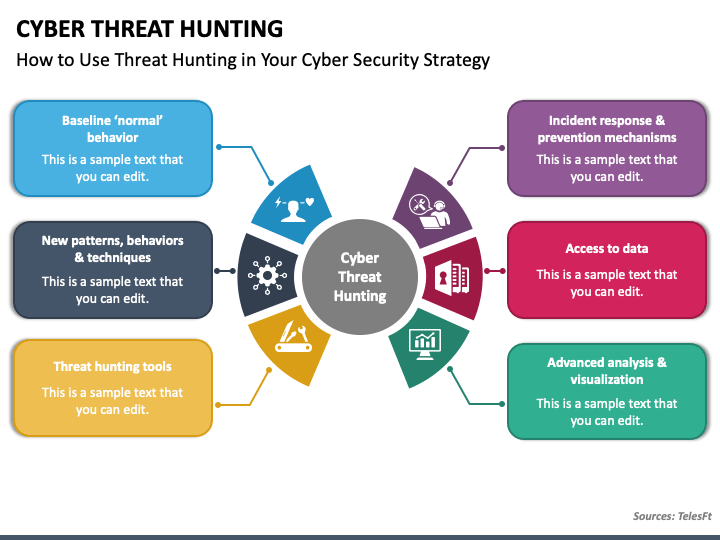
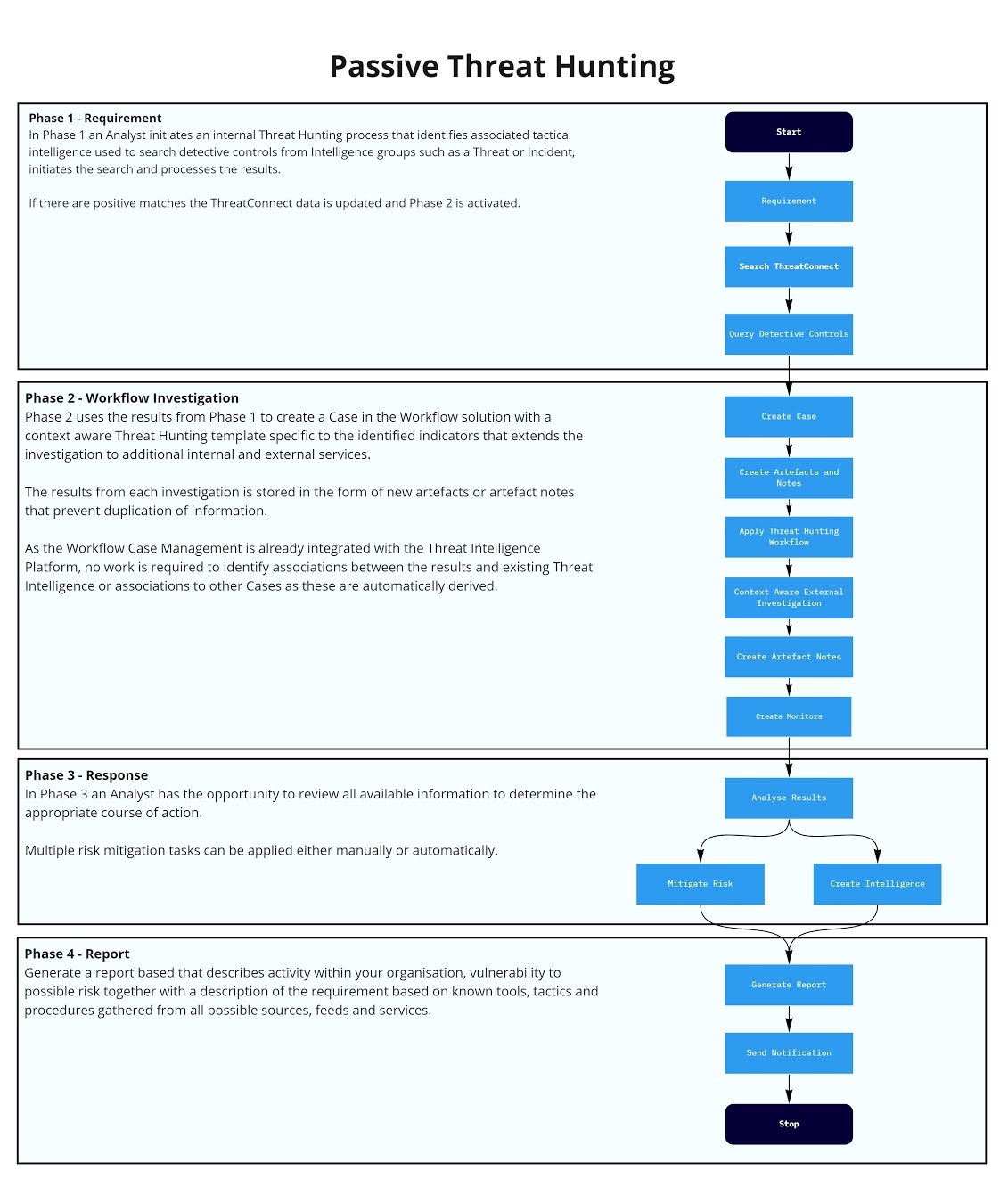
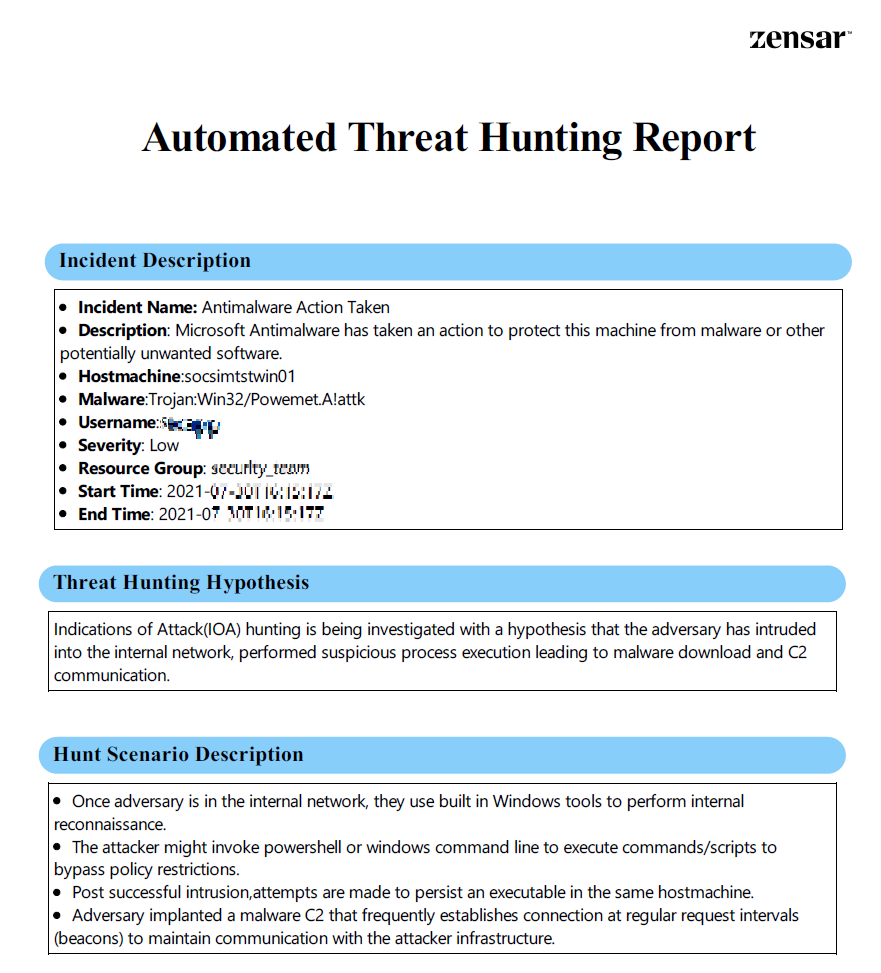
Threat Hunting Report Template
Threat Hunting Report Template - The following template for a. Cut junk data up to 50%shape data as needed This article aims to guide. A repository of kql queries focused on threat. My report template follows a pretty simple 2.
The following template for a. This article aims to guide. A repository of kql queries focused on threat. Cut junk data up to 50%shape data as needed My report template follows a pretty simple 2.
Cut junk data up to 50%shape data as needed My report template follows a pretty simple 2. This article aims to guide. A repository of kql queries focused on threat. The following template for a.
Threat Hunting Report Template
This article aims to guide. The following template for a. My report template follows a pretty simple 2. A repository of kql queries focused on threat. Cut junk data up to 50%shape data as needed
Threat Hunting Process, Methodologies, Tools And Tips
A repository of kql queries focused on threat. The following template for a. My report template follows a pretty simple 2. Cut junk data up to 50%shape data as needed This article aims to guide.
Threat Intelligence Platform Provider & Services GroupIB
My report template follows a pretty simple 2. The following template for a. A repository of kql queries focused on threat. This article aims to guide. Cut junk data up to 50%shape data as needed
What is Proactive Threat Hunting?
Cut junk data up to 50%shape data as needed My report template follows a pretty simple 2. The following template for a. A repository of kql queries focused on threat. This article aims to guide.
Threat Hunting Assessments
Cut junk data up to 50%shape data as needed This article aims to guide. A repository of kql queries focused on threat. The following template for a. My report template follows a pretty simple 2.
Threat Hunting Report Template
Cut junk data up to 50%shape data as needed This article aims to guide. My report template follows a pretty simple 2. A repository of kql queries focused on threat. The following template for a.
Ransomware As a Service What is It and How Can You Protect Your
The following template for a. A repository of kql queries focused on threat. This article aims to guide. My report template follows a pretty simple 2. Cut junk data up to 50%shape data as needed
Threat Hunting Report Template
Cut junk data up to 50%shape data as needed The following template for a. This article aims to guide. A repository of kql queries focused on threat. My report template follows a pretty simple 2.
Threat Hunting Process from Scratch Download Scientific Diagram
The following template for a. A repository of kql queries focused on threat. Cut junk data up to 50%shape data as needed My report template follows a pretty simple 2. This article aims to guide.
The Following Template For A.
My report template follows a pretty simple 2. This article aims to guide. Cut junk data up to 50%shape data as needed A repository of kql queries focused on threat.